C Password and security questions. What types of technologies are used by external motion detectors.
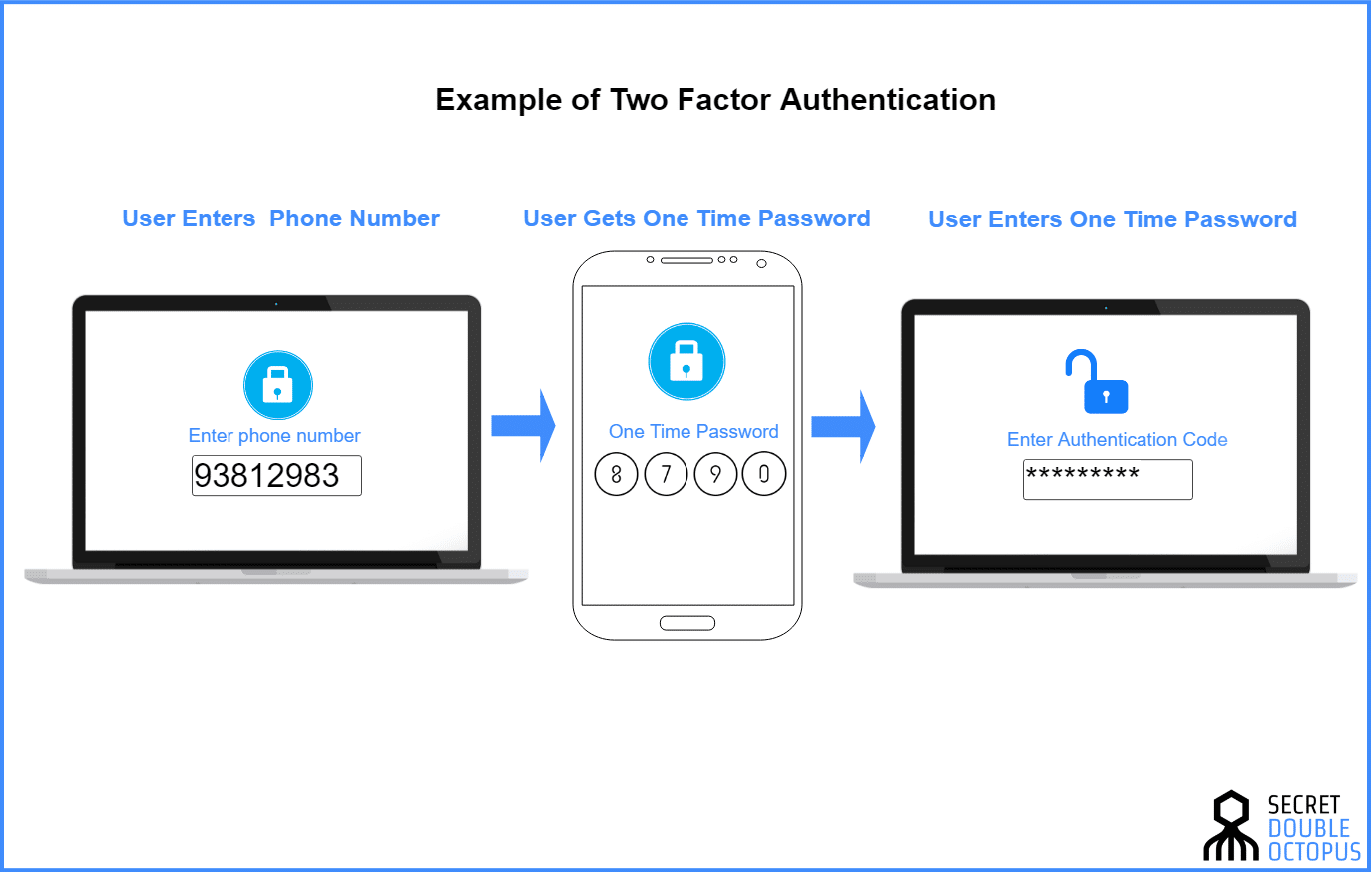
What Is Two Factor Authentication 2fa Security Wiki
Add acr client scope to your clients.

. Which of the following is an example of two-factor authentication. A fingerprint and a retina scan. A username and a password C.
Motion detectors often use infrared technology. Smart card and personal identification number PIN Authentication using smart cards and PINs is two-factor authentication because it combines ownership and knowledge. A Smart card and personal identification number PIN B Personal identification number PIN and password.
VPN is short for virtual private network. Computer Science questions and answers. Question 14 Which one of the following is an example of two-factor authentication.
Password text code c. We would like to show you a description here but the site wont allow us. Smart card and personal identification number PIN Authentication using Smart card and personal identification number PIN is an example of two-factor authentication because is involves a combination of both ownership and knowledge.
A Smart card and personal identification number PIN B Personal identification number PIN and password C Question. The type of authentication can vary but will generally be a username and password. Question 14 Which one of the following is an example of two-factor authentication.
A pass phrase and a PIN D. Using a security device with your password to gain access to Internet Banking. Googles Gmail has a security feature where it can send you a password reset link to an alternate email address if youve forgotten your password.
Photo ID smart card fingerprint Smart card digital certificate PIN. Two-factor authentication makes the user provide a password and one example of it is the personal identification. A token device and a PIN B.
This is an example of two-factor authentication. What is the best example of two factor authentication. Heat would set them off.
Smart cards and biometrics is an example of two-factor authentication. Thumbprint and key card. Two factor authentication factors enabling checklist.
Which of the following is the verification of a persons identity. QUESTION 76 Which of the following is an example of two factor authentication A from HISTORY 125 at Technical University of Cluj-Napoca. 2fa is implemented to better protect both a.
Using PINs passwords and security questions in any combination is single-factor authentication because all three are knowledge-based. Which one of the following is an example of two-factor authentication. Which of the following is an example of two-factor authentication.
7 hours agoIf you do not plan to use step-up authentication feature but you rely on the acr claim in the token you can disable step_up_authentication feature as described in the Server Installation and Configuration GuideThe claim will be added with the value 1 in case of normal authentication and 0 in case of SSO authentication. A pass phrase and a PIN A username and a password A fingerprint and a retina scan A token device and a PIN A token device and a PIN Which of the following is an example of threefactor authentication. QUESTION 76 Which of the following is an example of two factor authentication A.
Which of the following is not a common criteria when authenticating users. Which of the following is an example of two-factor authentication.
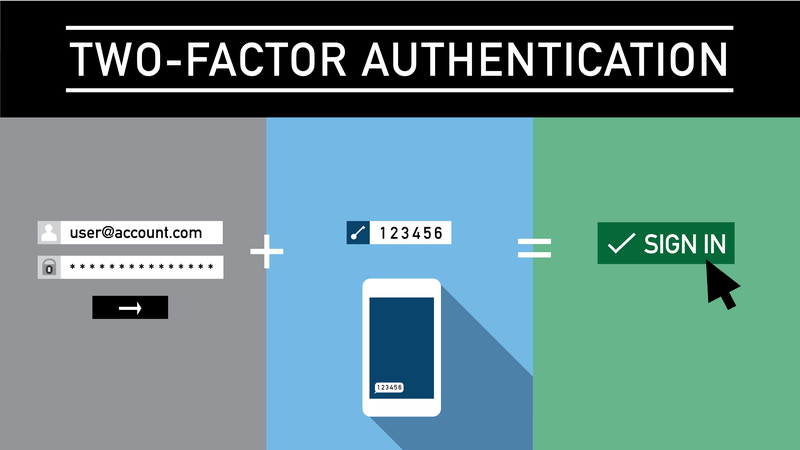
Two Factor Authentication For Beginners By Martin Shelton Medium

Duo Multi Factor Authentication Mfa Duquesne University
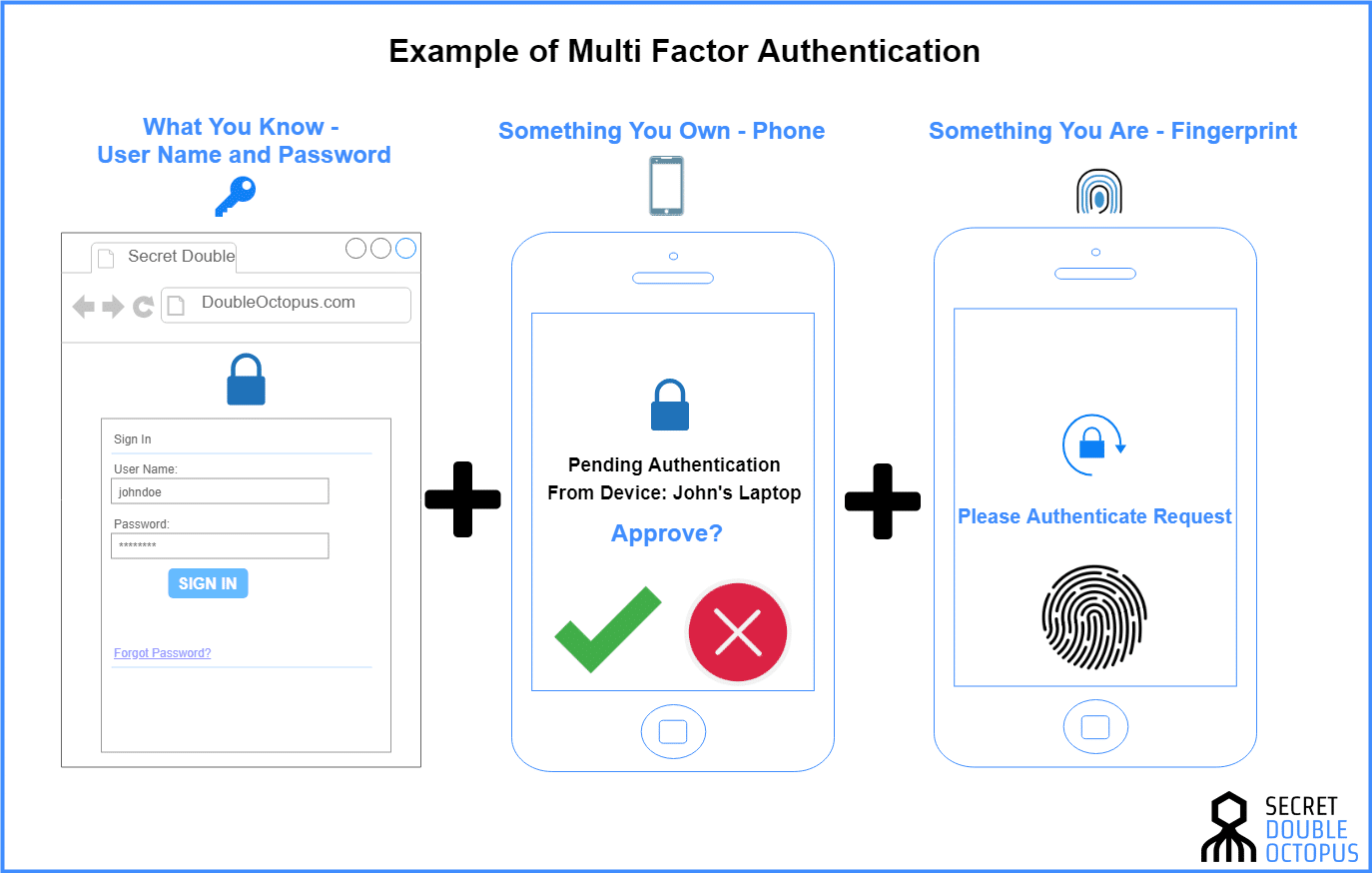
What Is Multi Factor Authentication Mfa Explained Security Wiki
0 Comments